Amazon SageMaker Studio adds web-based interface, Code Editor, flexible workspaces, and streamlines user onboarding | Amazon Web Services
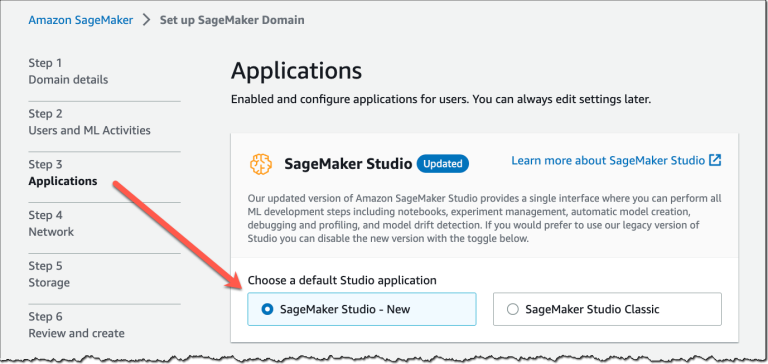
Today, we are announcing an improved Amazon SageMaker Studio experience! The new SageMaker Studio web-based interface…