Previously I explained how to encrypt Linux partitions or disk with the LUKS (Linux Unified Key Setup)/dm-crypt. In this quick blog post, I will explain how to backup and restore LUKS header for emergency purposes. Backup is useful for recovering from misconfigurations, corrupted headers or forgotten passphrase or unknown password.
Why backup and restore LUKS header on Linux?
LUKS is a standard method on Linux based system for protecting data and disk, especially on mobile devices such as Linux laptop. However, LUKS also create additional challenges, such as:
- LUKS misconfiguration of both /etc/fstab or /etc/crypttab file will prevent booting your Linux based laptop. These files provide hints for decryption while booting the system. The file /etc/crypttab contains descriptive information about encrypted filesystems, which is only read by LUKS programs. The Linux system administrator has to create and maintain this file appropriately.
- Verify that /etc/fstab and /etc/crypttab is correct and entries matched as per your setup using the cat command:
cat /etc/fstab /etc/crypttab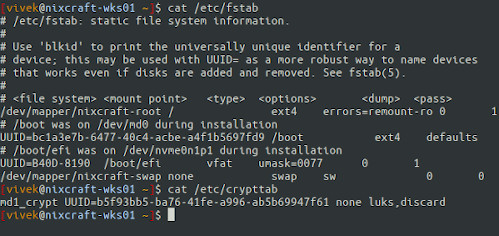
- A forgotten password or passphrase may cause the LUKS decryption failure at boot time. Currently, there is no way to recover LUKS passphrase. Sometimes sysadmin or user changes their LUKS password to an unknown value. Please note that LUKS currently allows a total of eight passphrase or key slots for encrypted disks. Linux sysadmin can use those keys or passphrases if created to reset the forgotten password. However, if a backup of the LUKS header exists, we can restore the header from backup and use a previously working passphrase/password.
Dealing with LUKS encrypted disks or volumes
Let see how to create LUKS header backup and restore it in case the need arises later. To list encrypted disks or volumes, enter:$ sudo dmsetup ls --target crypt
[sudo] password for vivek: md1_crypt (253, 0)
Run the lsblk command:$ lsblk
$ lsblk /dev/md1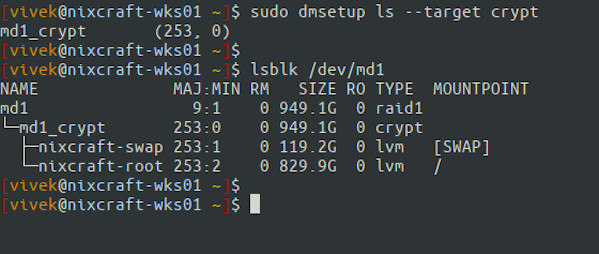
So /dev/md1 is Linux software RAID1 device and encrypted as md1_crypt. Further, LVM is used to create root and swap partitions. In other words, my root and swap are fully encrypted and protected with RAID1. Next, list your /etc/fstab and /etc/etc/crypttab too and make sure they are correctly mapped:$ cat /etc/fstab
$ cat /etc/etc/crypttab
Your setup might be simple without RAID1 or LVM. Hence, you need to find out the exact information.
To recover data from encrypted file/volumes backup the following files
- /etc/fstab file
- /etc/crypttab file
- LUKS header
Step 1 – Duping up LUKS header
Run the command to find out information about the encrypted disks or volume$ sudo cryptsetup luksDump /dev/DEVICE
$ sudo cryptsetup luksDump /dev/sdb2
$ sudo cryptsetup luksDump /dev/md1
LUKS header information Version: 2 Epoch: 3 Metadata area: 16384 [bytes] Keyslots area: 16744448 [bytes] UUID: b5f93bb5-ba76-41fe-a996-ab5b69947f61 Label: (no label) Subsystem: (no subsystem) Flags: (no flags) Data segments: 0: crypt offset: 16777216 [bytes] length: (whole device) cipher: aes-xts-plain64 sector: 512 [bytes] Keyslots: 0: luks2 Key: 512 bits Priority: normal Cipher: aes-xts-plain64 Cipher key: 512 bits PBKDF: argon2i Time cost: 4 Memory: 673681 Threads: 4 Salt: 1e 68 17 ca 2c c5 b5 fa 2b 8b 59 6a 73 ca 1c 20 f7 99 06 63 4e fa 49 3d 12 71 ac 6a bb 41 ec 58 AF stripes: 4000 AF hash: sha256 Area offset:32768 [bytes] Area length:258048 [bytes] Digest ID: 0 Tokens: Digests: 0: pbkdf2 Hash: sha256 Iterations: 145635 Salt: 95 2c 81 91 8c 1e ad 69 4d 51 18 13 4c 36 c0 25 c5 5c 9d 16 c3 0f 3f 79 fa 84 ad 4b 65 49 17 ec Digest: 79 8a 05 d0 31 ba 7a ec fe f2 b1 da 3f d8 17 e1 eb f8 2c b1 a7 7e ed 26 59 9e 7a 02 b3 95 0c 03 |
Step 2 – Backing up LUKS header
Make a backup of your LUKS header for future use:$ sudo cryptsetup luksHeaderBackup /dev/DEVICE
--header-backup-file /path/to/backupfile
$ sudo cryptsetup luksHeaderBackup /dev/sdb2
--header-backup-file /nas/vivek/laptop.dell.m6700.luks.bin
$ sudo cryptsetup luksHeaderBackup /dev/md1
--header-backup-file /root/laptop.thinkpad.luks.bin
Show information about backup file named /root/laptop.thinkpad.luks.bin, run the following file command/stat command/cryptsetup command:$ sudo file /root/laptop.thinkpad.luks.bin
$ sudo stat /root/laptop.thinkpad.luks.bin
$ sudo cryptsetup luksDump /root/laptop.thinkpad.luks.bin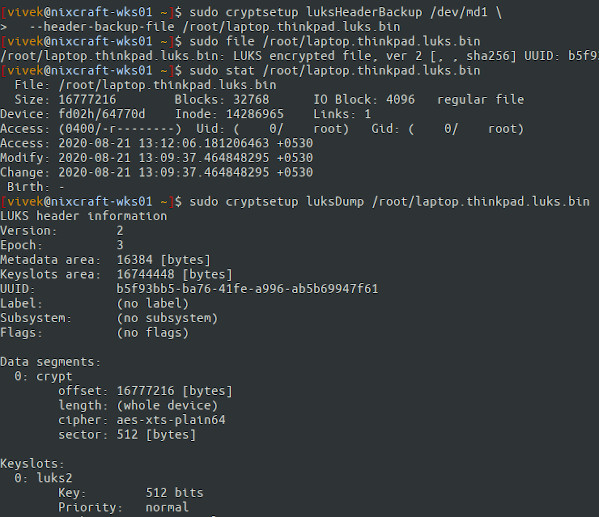
Make sure you store laptop.thinkpad.luks.bin file securely offline. I use NAS server and USB stick. Make sure you store your backup file named /root/laptop.thinkpad.luks.bin file securely offline. I use my home NAS server and USB stick. This file must remain off the device; otherwise, you may not be able to restore it.
Step 3 – Restoring LUKS header when needed
Now let us say something terrible happened. All you have to do is boot your system/laptop from a boot disk and restore the old LUKS header from the laptop.thinkpad.luks.bin backup file as follows:# cryptsetup luksHeaderRestore /dev/DEVICE --header-backup-file /path/to/backup_header_file
## Assuming that you mounted /nas/ using NFS ##
# cryptsetup luksHeaderRestore /dev/md1 --header-backup-file /nas/vivek/laptop.thinkpad.luks.bin
WARNING! ======== Device /dev/md1 already contains LUKS2 header. Replacing header will destroy existing keyslots. Are you sure? (Type uppercase yes): YES
Step 4 – Test it
Run the following command to open the encrypted disk and mount it (you need to provide old password):# cryptsetup luksOpen /dev/DEVICE name
# cryptsetup luksOpen /dev/md1 test
# mkdir /test
# mount /dev/mapper/test_root /test
# df -H
# mount
Reboot the Linux system:# reboot
Conclusion
You learned about various files and procedures to backup and restored LUKS headers if there was any misconfiguration or unknown, forgotten password on Linux based system. Each setup is unique and different. I hope this guide provides you enough material to successfully backup and restore a secured filesystem when needed. See the cryptsetup project for more documentation.
- Linux Hard Disk Encryption With LUKS
- Backup and restore LUKS header on Linux