The 2020 IoT Signals Report reveals 95 percent of IoT projects fail at proof of concept (PoC), with a significant portion due to the inability to scale despite the existence of many claims touting zero-touch provisioning. Imagine the following winning alternative instead: an IoT solution builder receives a batch of devices from its original equipment manufacturer (OEM) and all they do is power them to get the following:
- Automatic and secure onboarding to a production certificates provider.
- Receipt of device operational certificate credentials.
- Automatic provisioning to cloud application services.
- Automation of credentials renewal and lifecycle management.
More so, this seamless process is the same for all devices, whether in PoC or the millionth in production, and the best part is that setup requires only three simple one-time non-engineering actions by the solution builder. This is exactly what we’ve accomplished with partners and now present how as a blueprint.
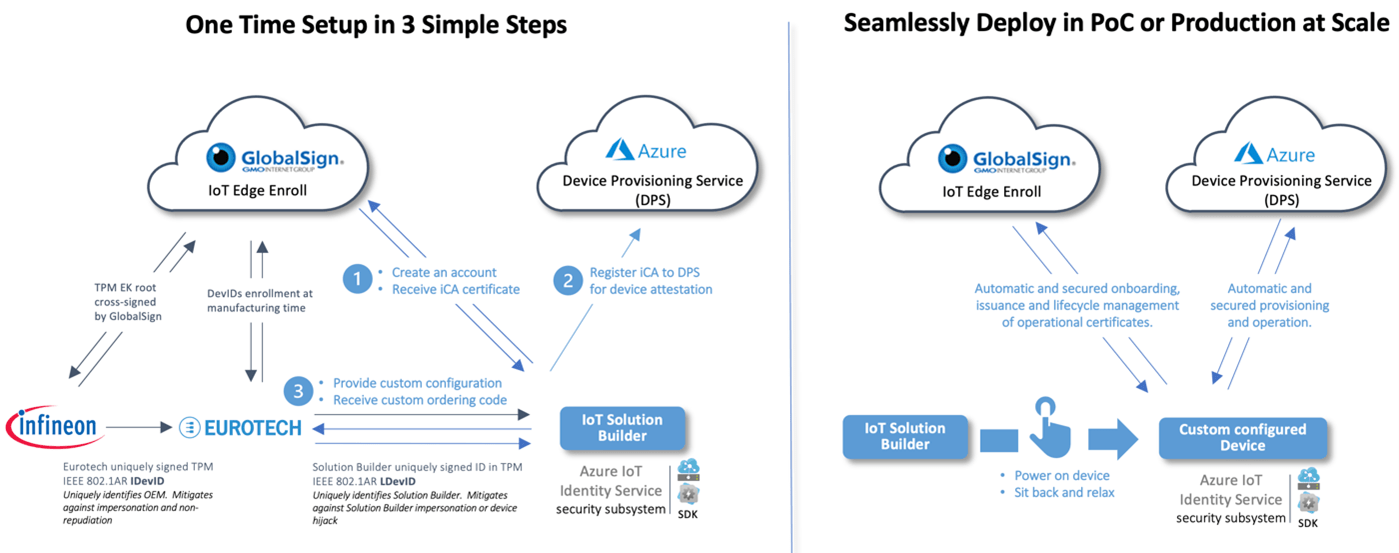
Figure 1: Seamlessly and securely deploy at scale from a one-time setup in three simple steps—a solution blueprint to zero-touch provisioning
For this ease, all the solution builder does for setup is create an account with the managed credential provider, deliver device customization instructions to the OEM, and register an attestation certificate to Azure Device Provisioning Service (DPS). They perform each of these actions only once to enable a zero-touch provisioning experience that is true for both PoC experience and production deployments at scale. What the solution builder may not and need not know is the preceding complex integrations comprise an interplay of multiple certificate credentials in a trust delegation to accommodate the multi-custodial nature of the device manufacturing value chain, security hardening to resist tampering, and priming for automated renewal and lifecycle management of operational credentials. True scalable zero-touch provisioning can result only after these complex integrations occur; otherwise, the burden falls on the internet of things (IoT) solution builder and hence the observed high failure rate.
But why is zero-touch provisioning so elusive?
Simply put, zero-touch provisioning requires a narrow understanding of the provisioning needs for IoT devices. This is not a criticism but rather an observation that might be indicative of evolution and maturity in IoT practices. A true solution will never emerge without a proper understanding of the problem space.
A holistic view of IoT provisioning must recognize IoT projects which exist in phases and must consider these phases when designing a zero-touch provisioning experience. For illustrative simplicity, let’s break down the project into three phases, namely evaluation, deployment, and operational, but knowing one could get even more granular.
The evaluation phase
The evaluation phase kickstarts every project and entails the creation of a PoC. It is characterized by the solution builder having full control of the development environment and working with pre-existing devices in unitary quantities. By virtue of the full control of the development environment, provisioning entails embedding a credential into the device. This allows the builder to take comfort in the security because only they have knowledge of the credential and they are the only one who has physical possession of the device.
The deployment phase
Next comes the deployment phase which entails device manufacturing for production scale. This phase expands the development environment into an ecosystem of device manufacturing and supply chain partners. It also expands device quantities by several orders of magnitude. A clear characteristic of the deployment phase is a shift of control from full ownership of the solution builder to shared ownership with partners. Security demands strong actions to protect confidential information within the solution by preventing the accidental sharing of information, allowing for increased trust in partner interactions. To uphold security and trust, provisioning must entail multiple credentials for knowledge amongst partners, a trust delegation scheme as the device changes custody, and security hardening to help prevent tampering.
The operational phase
The operational phase returns control to the IoT solution builder and entails the solution operation and lifecycle management of credentials and devices. The role of provisioning in this phase is the setup that divorces the value chain of manufacturing partners to focus on operation (hence how the solution builder regains control), provisions operational credentials, and enables lifecycle management actions such as renewal, revocation, and retirement.
Provisioning of IoT devices is therefore a complex undertaking in security and building trust within an open ecosystem. Consequently, getting provisioning right demands a comprehensive understanding of the multi-faceted nature of the problem and acknowledgment that a complete solution will require several fields of expertise. Sadly, most claims of zero-touch provisioning only address the needs of the evaluation phase and ignore the needs of the deployment and operational phases that are requisite for at scale production. It is no wonder why the experience of zero-touch provisioning is elusive.
Call in the experts
Complex problems are best solved by domain experts. Solving for zero trust provisioning requires expertise from many domains top of which are experts in operating public key infrastructures (PKI), hardening security, and customizing devices in a standard device manufacturing and acquisition process.
Expertly operating a PKI is a fundamental requirement of zero-touch provisioning. A PKI service suitable for onboarding and operation of IoT devices at scale amongst many attributes needs to be highly available, provide global coverage, enable certificates audits, and deliver lifecycle management actions such as renewal and revocation. Above all, the PKI service should assist in achieving data sovereignty goals. An expertly operated PKI is important for many reasons. First, the underlying asymmetric-key cryptography provides the foundation for a zero trust model of partner collaboration within a devices’ value chain. The fact that each partner holds a private key that they never share provides the basis for exclusive trust. Secondly, PKI enables IoT to benefit from decades of experience in enterprise IT practice of issuance and lifecycle management of certificate-based device credentials. Certificate-based credentials are valued over alternative forms of credentials because they also build on asymmetric-key cryptography to enforce a zero trust model of computing in IoT. Operating a PKI builds on these two concepts and requires heavy responsibilities only dedicated experts can deliver. Certificate Authorities (CA) possess the requisite expertise from long practices in IT.
Security hardening complements a well-planned and structured PKI in resisting tampering. It is not a secured solution without countermeasure to subversion which is the goal of tamper resistance. Tamper resistance derives from a very special class of integrated circuits whose primary goal is to operate normally or fail predictably under all adversity be it physical, environmental, or networked. The result is mitigation against subversion, hijack, infiltration, and exfiltration. These tamper-resistant integrated circuits commonly known as hardware security modules or simply HSMs. The well-honed art of producing and prescribing proper application HSMs demands expertise that is provincial to only a subset of semiconductor silicon manufacturers.
Device personalization through customization is the final element to achieving secured zero-touch provisioning and demands domain expertise of OEM. The OEM must work in concert with the PKI and HSM providers to assure certain goals. First, that trust initiates and properly transits various custodians in the device manufacturing value chain. Second, that the device is customized to the solution builders’ specifications and to seamlessly connect to the right cloud solutions. Third, that the device automatically onboards and transition into operational states complete with proper credential provisioning and lifecycle management. Fourth, that the device is hardened against impersonation. Finally, that the device procurement process remains simple. Delivering secured devices in simplicity is a difficult balance that commands expertise and experience.
Finally, it takes the right IoT product base, with features purposefully designed in, to leverage expertise from the various domains and exclusively through the use of standards where available. The IoT Identity Service security subsystem for Azure IoT Edge accomplishes this goal.
The blueprint
For this blueprint we allied with the Certificate Authority (CA) and PKI services provider, Global Sign, the semiconductor manufacturer and HSM maker, Infineon Technologies, and OEM and edge device integrator, Eurotech. The technical integration builds on the modular IoT Identity Service security subsystem of Azure IoT Edge where the domain experts leveraged features such as the IETF RFC 7030 Enrollment over Secure Transport (EST) built-in client standard for certificates requests, the ISO/IEC 11889 Trusted Platform Module (TPM) and PKCS#11 interface standards for HSM integration, and the modularity of the security subsystem to accommodate the diversity of existing device manufacturing flows which is a very important consideration. The goal is not to disrupt decades-old existing manufacturing supply chains but to build on their respective experiences. This allied integration spares the IoT solution builder from delving into requisite domain expertise and assures a solution that is secured by default. The result is a device highly customized for the IoT solution builder who need not do more on receipt than to turn it on.
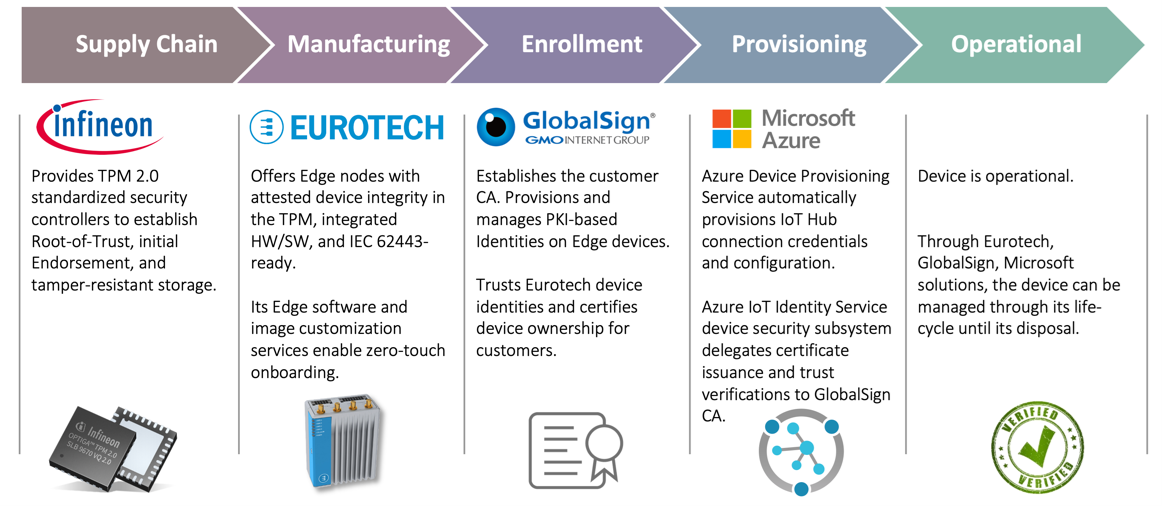
Figure 2: Integrated trust from TPM to cloud for security and integrity from supply chain to services
The blueprint is thus about domain experts allying to solve the problem for the IoT solution builder and in doing so assures proper application of various technologies for a comprehensive solution to zero-touch provisioning at scale. For this integration, trust truly initiates from the source of the value chain which is the Infineon Technologies TPM. For example, Global Sign can authoritatively verify that the target TPM is in fact one manufactured by Infineon Technologies because of prior TPM manufacturing certificate cross-signing as part of pre-verification to issuing operational certificates.
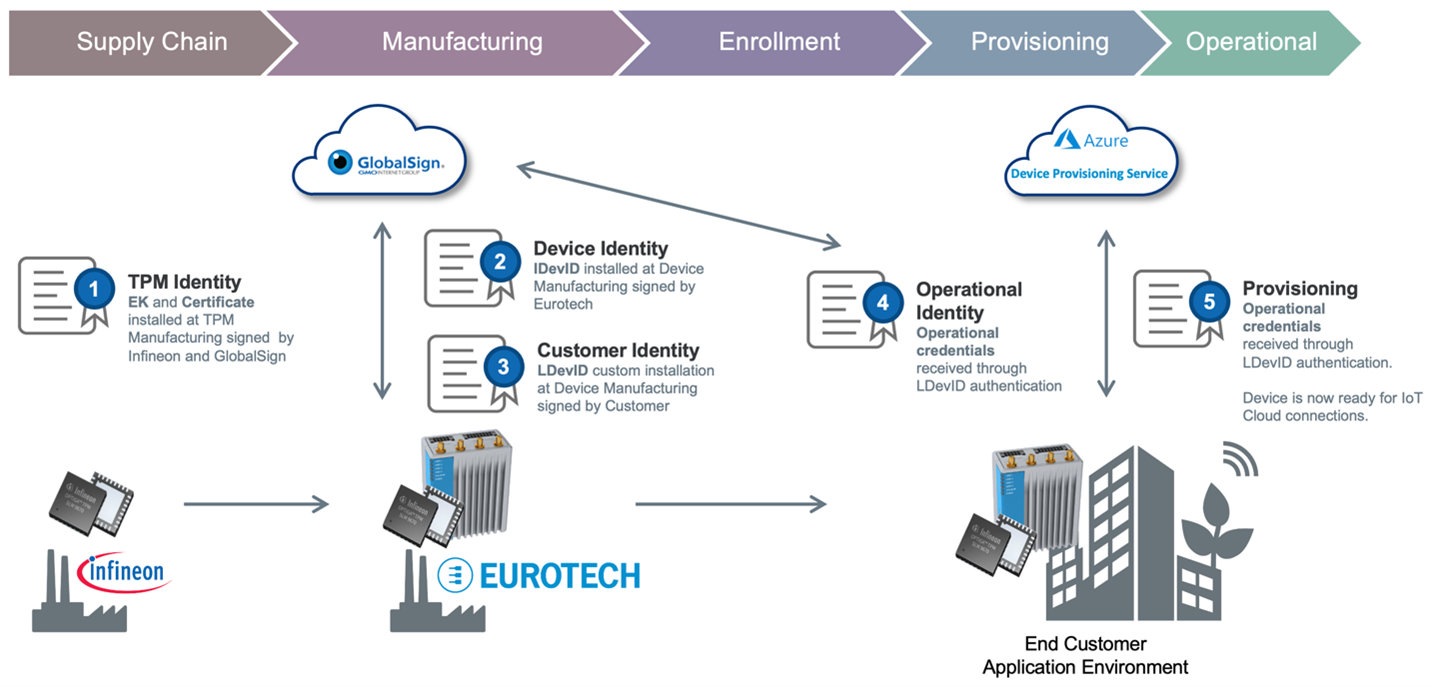
Figure 3: The IoT device identity lifecycle involves multiple credentials
This alliance of partners has composed a joint whitepaper that outlines the security and engineering principles that underlie this solution in the spirit of presenting a blueprint for replication.
Why standardization is important
Zero-touch provisioning is a difficult problem that truly calls for standardization. The difficulty might stem from several reasons but an obvious one is how to build a solution standard on a very diverse base of manufacturing flows without coercing expensive restructuring and retooling. No problem lasts forever and someday a standard will emerge. Until then, why not build on existing standards (such as TPM, X.509, PKCS#11, EST), manufacturing flows, and value chains to create microcosms of technology alignments and pragmatically solve a clear and present problem? This is the essence of the blueprint which in addition to providing a pragmatic solution for the moment, is a call to the rest of the industry to unite in standardization.
Bringing IoT solutions to production
Many solutions that claim zero-touch provisioning in IoT lead to failures in PoC because they fail to solve the challenges that underlie IoT provisioning at scale. The right solution requires a comprehensive undertaking that must employ expertise from several domains to overcome complex challenges and deliver secured and seamless zero-touch provisioning at scale. Complex problems of this nature are often solved by uniting forces in standardization. However, many consortia have been at this problem for several years without tangible results, presumably because a high risk of forcing a highly diverse device manufacturing flows into untenable expensive restructuring for compliance. This blog offers a comprehensive solution to zero-touch provisioning by an alliance of experts presented here as a blueprint that builds on existing experiences and manufacturing flows to raise the success rate of IoT solutions going into production.
To all the domain experts in the IoT value chain, this is a call to recognize the shared responsibility requisite of secured IoT solution deployments. We all win when the solution builder is successful so let us all team up in alliances to bring about truly secured and comprehensive zero-touch provisioning in production at scale or simply join us in Azure. It is the blueprint for success.
To all IoT solution builders, ask your OEM partners to align with partners and deliver devices with the pre-integrations described in this blueprint to help simplify the experience of securely scaling the solution from PoC to production.




