NetEase to shut down public cloud service amid rising AI competition
NetEase is discontinuing one of its public cloud services as competition in China’s cloud computing market…

NetEase is discontinuing one of its public cloud services as competition in China’s cloud computing market…

The digital transformation landscape has seen cloud migration services become a key strategy for businesses seeking…

🔥 Want to try out one of the best VPN options? Grab a discount! 🔥✅ Get…

On April 27, 2007, a massive cyberattack was launched against Estonia. Not some of its citizens,…

Introduction For decades, Linux and BSD have stood as two dominant yet fundamentally different branches of…
Introduction Linux is a powerful and flexible operating system, widely used in servers, embedded systems, and…

Enterprise apps and business AI specialist, SAP, has unveiled SAP Business Data Cloud, which unifies all…

In this video, we’re bringing you the biggest cybersecurity stories of the week.🥷 Check out a…

#mwc25 #fyp #cybernews If you find this video interesting, don’t forget to like, share, and subscribe…

The i18n team is testing changes for Fedora Linux 42 (ibus-libpinyin 1.16, IBus 1.5.32, and many…
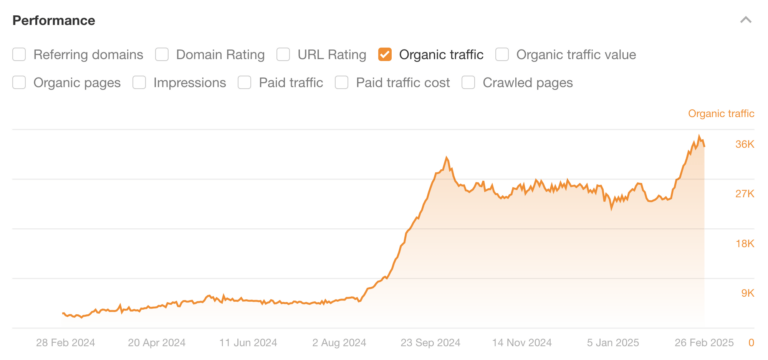
We’ve analyzed 150K websites to find out which ecommerce startups have seen substantial search growth this year….

The HIPAA (Health Insurance Portability and Accountability Act) continues to make a significant impact on the…

Introduction In the ever-evolving digital world, Linux servers form the backbone of enterprises, web applications, and…

#humanoidrobot #creepy If you find this video interesting, don’t forget to like, share, and subscribe for…

In the fast-evolving world of finance and taxation, AI-powered tax tools have become indispensable for individuals,…

#funfacts #fyp #cybernews If you find this video interesting, don’t forget to like, share, and subscribe…

Introduction Memory management is a critical aspect of modern operating systems, ensuring efficient allocation and deallocation…

In this video, we’re bringing you the biggest cybersecurity stories of the week.🥷 Check out a…