VMware UAG: Two-Factor Authentication configuration

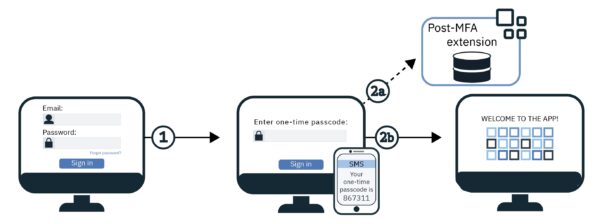
To add an extra layer of security to VMware UAG appliance, the authentication process can be enforced using a Two-Factor Authentication procedure with solutions such as Duo Authentication Proxy.
If the UAG appliance is installed in your VMware Horizon infrastructure, the Two-Factor Authentication makes the connection more secure avoiding unauthorized accesses. Duo is Cisco’s user-friendly, scalable access security platform that can be configured in the UAG appliance providing a second source of validation.
System requirements
DUO Authentication Proxy can be installed on the following supported OSs:
- Windows Server 2012 or later (Server 2016 or 2019 recommended)
- CentOS 7 or later
- Red Hat Enterprise Linux 7 or later
- Ubuntu 16.04 or later
- Debian 7 or later
The minimum system requirements are the following:
- Form Factor: physical or virtual machine
- Processor: 1 processor
- Memory: 4 GB RAM
- Disk: 200 MB or greater
The Authentication Proxy communicates with Duo’s service on TCP port 443. Make sure to open firewall ports accordingly.
The Duo Mobile app must be installed on your mobile device (Android or Apple) to manage push notifications.
Install DUO for Two-Factor Authentication
DUO can be installed on both Windows or Linux OSs and the procedure is pretty straightforward. To save Windows licenses, the Duo MFA can be easily installed on a supported Linux distributions.
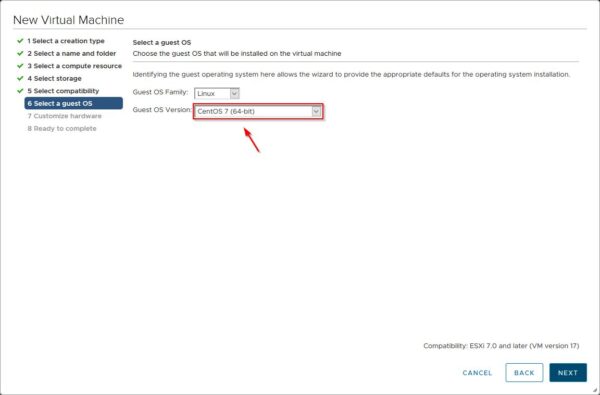
Deploy CentOS OS
Download the minimal installation of CentOS 7 and deploy the VM on your LAN.
Install DUO Authentication Proxy
SSH the CentOS 7 VM and run the following command from the console to install the needed packages:
# yum install gcc make libffi-devel perl zlib-devel wget
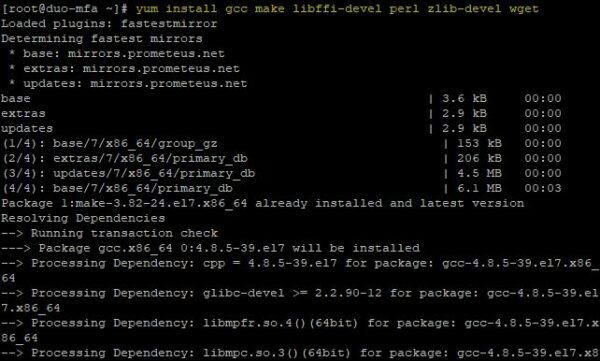
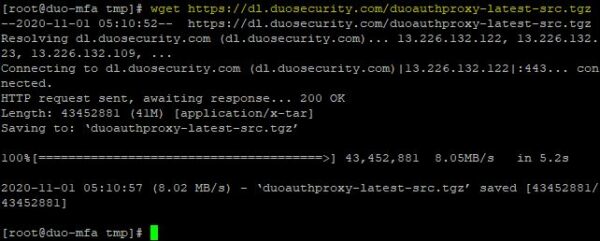
Download the Authentication Proxy module using the wget command.
# wget https://dl.duosecurity.com/duoauthproxy-latest-src.tgz
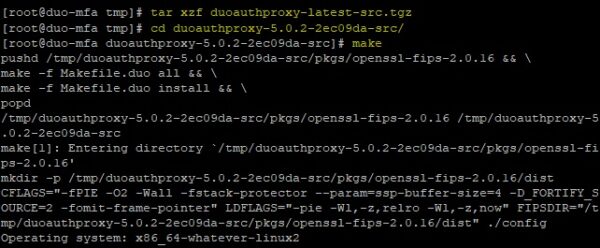
Extract the files from the downloaded file .TGZ and run the build process.
# tar xzf duoauthproxy-latest-src.tgz
# cd duoauthproxy-version-src
# make
When the build process has completed successfully, run the install command to install the application.
# cd duoauthproxy-build
# ./install
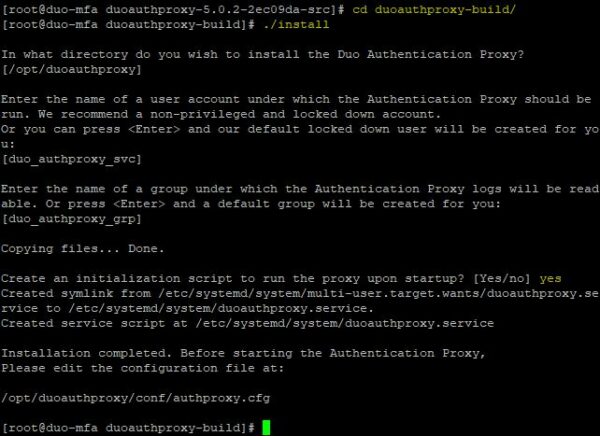
Note that the Duo Authentication Proxy’s configuration file is stored in the directory /opt/duoauthproxy/conf/authproxy.cfg.
Retrieve Duo parameters
After registering the account in Duo, select the software to protect (VMware View) from the available applications list.
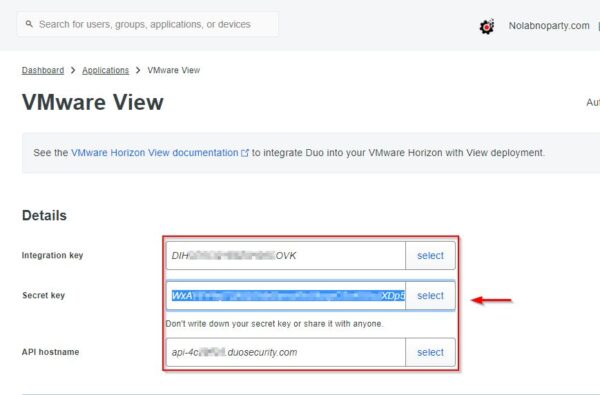
Access the application area and write down the parameters reported in the Details area needed to configure Duo:
- Integration key
- Secret key
- API hostname
Configure the push authentication
Duo provides different authentication methods you can configure. The push notification for example allows the application to send a push notification directly to the user’s mobile device.
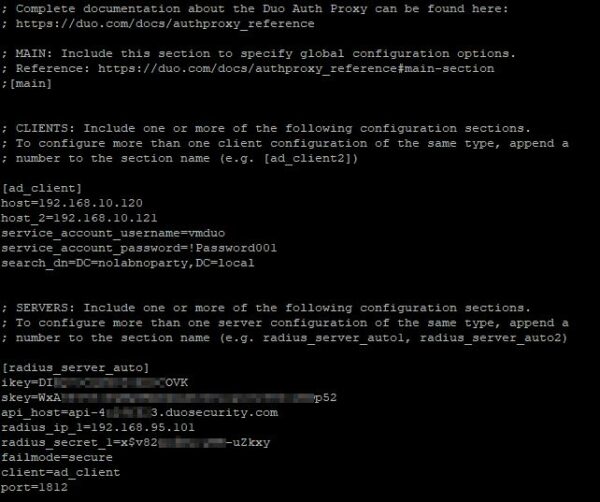
To configure the push notification, you need to edit the Duo’s configuration file and configure it as follow:
# vi /opt/duoauthproxy/conf/authproxy.cfg
[ad_client]
host=xx.xx.xx.xx (IP Domain Controller 1)
host_2=xx.xx.xx.xx (IP Domain Controller 2)
service_account_username=duoservice
service_account_password=password
search_dn=DC=domain,DC=com
[radius_server_auto]
ikey=xxxxxxxxxxxxxxxxxxxx
skey=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
api_host=api-xxxxxxxx.duosecurity.com
radius_ip_1=192.168.95.101 (UAG1 IP address)
radius_ip_2=192.168.95.102 (UAG2 IP address)
radius_secret_1=xxxxxxxxxxxxxxxxxxxx (configure secret also in UAG)
failmode=secure
client=ad_client
port=1812
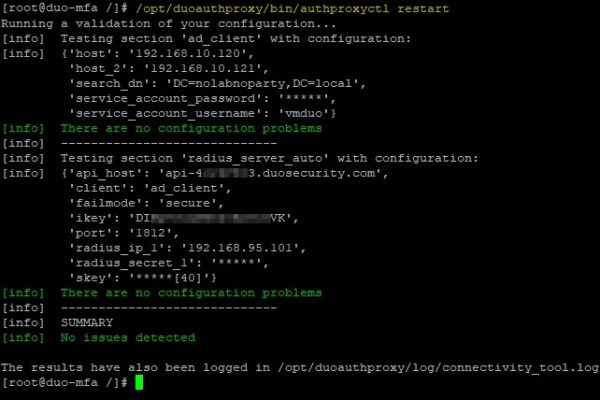
Save the file and restart the service.
# /opt/duoauthproxy/bin/authproxyctl restart
Configure UAG
Once the DUO Authentication Proxy has been configured successfully, the UAG must be configured accordingly.
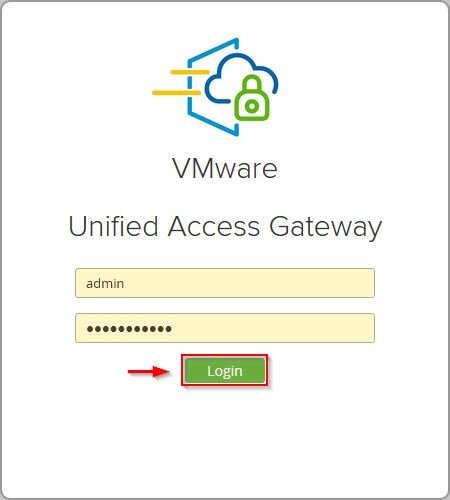
Using your preferred browser, type the addess https://<IP_UAG>:9443, enter the admin credentials and click Login.
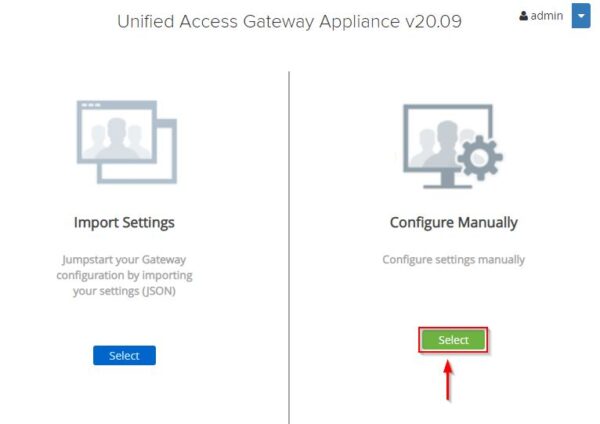
Click Select under Configure Manually.
Configure RADIUS
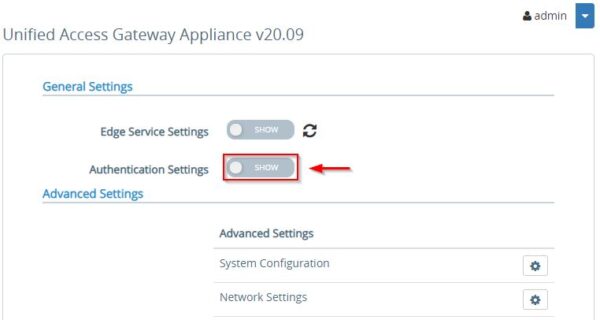
To take benfit of Duo Two-Factor Authentication, you need to access the Authentication section in UAG and configure RADIUS as protocol.
To set the RADIUS protocol enable the Authentication Settings switch.
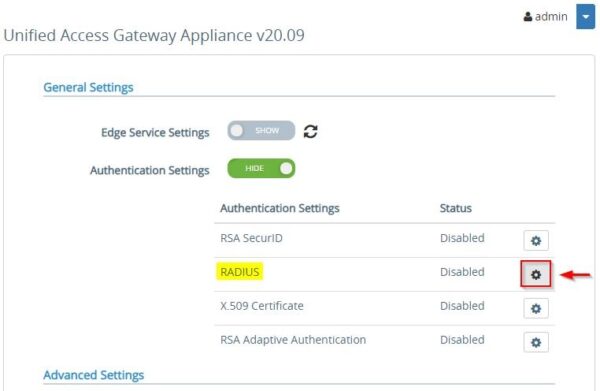
Click on the RADIUS Settings icon to configure the protocol.
Click on Enable RADIUS switch.
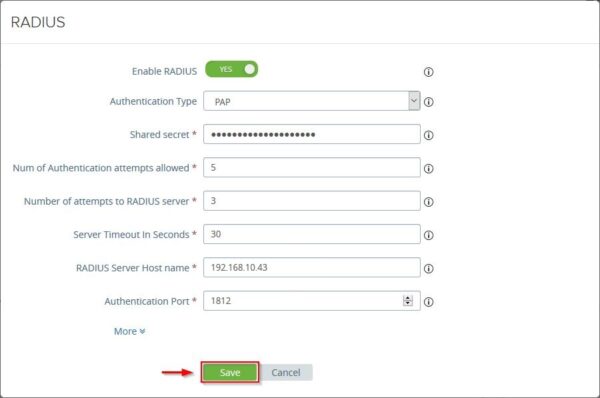
Configure the required parameters and click Save. The Shared Secret must be the same as configured in Duo Authentication Proxy.
Enable RADIUS authentication in UAG
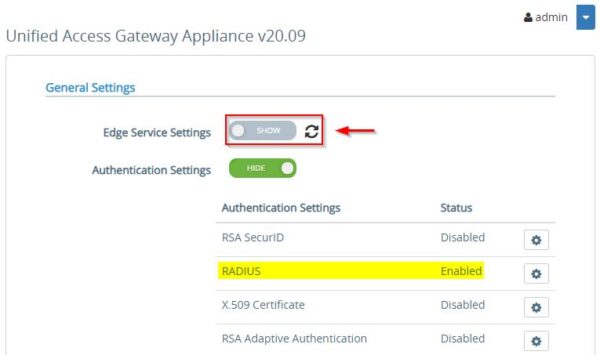
Once the protocol has been enabled, RADIUS must be configured in the Horizon’s settings. Click Edge Service Settings.
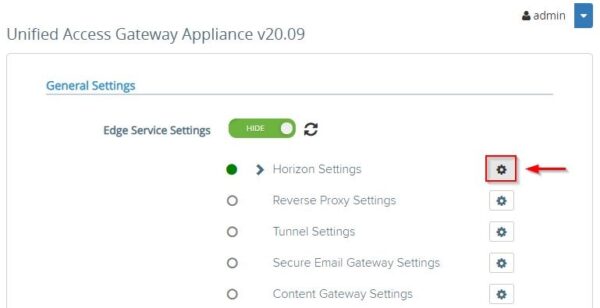
Click the Horizon Settings icon.
From the Auth Methods drop-down menu select RADIUS and click Save. You need to click the More link to display additional settings.
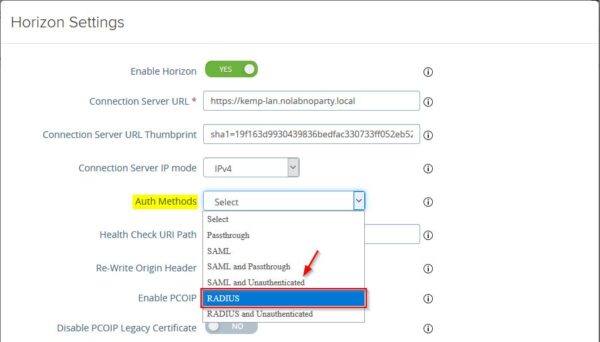
You need also to enable the these settings to avoid entering the credentials twice.
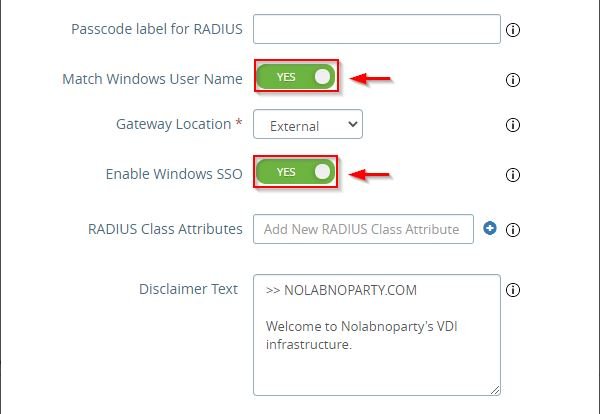
Test authentication
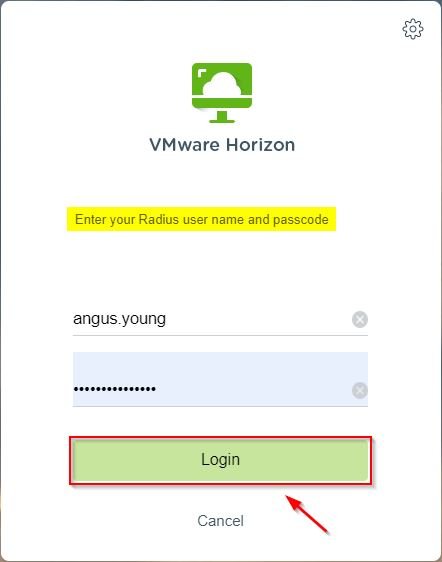
Open your preferred browser (for https access) and type the URL to access your Horizon infrastructure. Enter the credentials of an entitled user and click Login. Credentials are verified and authenticated against Active Directory.
Once the account has been validated in AD, a push request is then sent to the user’s mobile. Click Approve to login.
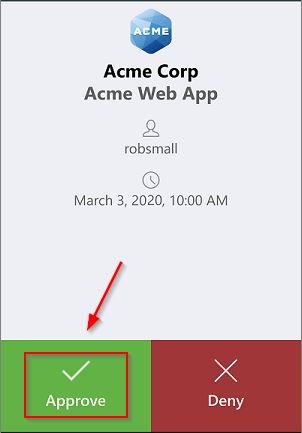
When the authorization has been given via Duo, the access to Horizon is granted.
UAG is now configured with Two-Factor Authentication making the access to your infrastructure more secure.