Transmission Control is an essential aspect of network activity and governs the behavior of many services we take for granted. When sending your emails or just browsing the web you are relying on TCP to send and receive your packets in a reliable fashion. Thanks to two DARPA scientists, Vinton Cerf and Bob Kahn who developed TCP/IP in 1970, we have a specific set of rules that define how we communicate over a network. When Vinton and Bob first conceptualized TCP/IP, they set up a basic network topology and a device that can interface between two other hosts.
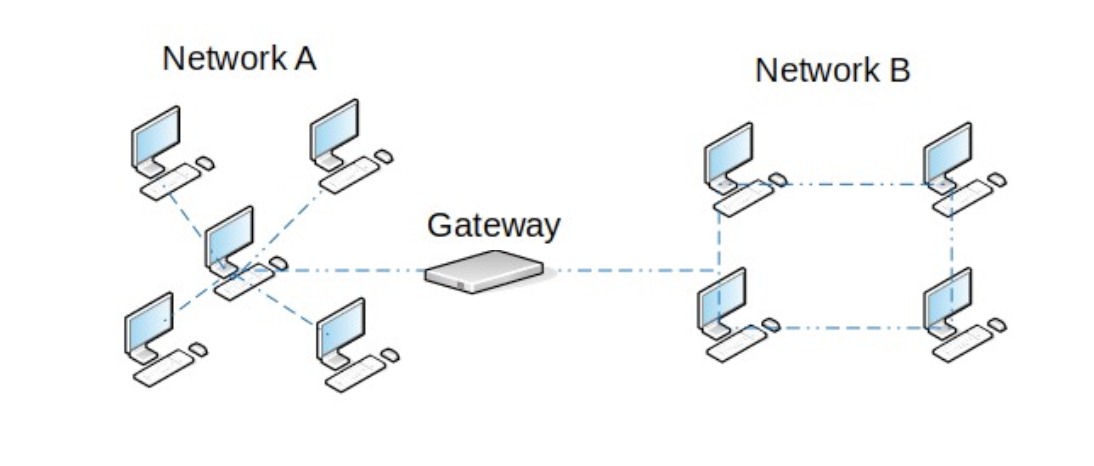
In the Figure 1 we have two networks connected by a single gateway. The gateway plays an essential role in the development of any network and bares the responsibility of routing data properly between these two networks.
Since the gateway must understand the addresses of each host on the network, it is necessary to have a standard format in every packet that arrives. Vince and Bob called this the internetwork header prefixed to the packet by the source host.

The source and destination entries, along with the IP address, uniquely identify every host on the network so that the gateway can accurately forward packets.
The sequence number and byte count identifies each packet sent from the source, and accounts for all of the text within the segment. The receiver can use this to determine if it has already seen the packet and discard if necessary.
The check sum is used to validate each packet being sent to ensure error free transmission. This checksum uses a false header and encapsulates the data of the original TCP header, such as source/destination entries , header length and byte count .
You can imagine that the sheer size and resource cost of sending large amounts of information through a single channel will grow exponentially. With memory constraints and transmission limitation it seems wise to split each packet into carefully selected fragments, each with its own sequence number, byte count and checksum, then reassemble the final packet at the destination host. Not only does fragmentation reduce costs of transmission, but it increases reliability of the data being transmitted as well as the speed of transmission. Of course never exceeding Shannon’s limit. However fragmentation introduces other complications such as proper packet sequence determination, proper sizing of each packet, dropped packets also require re-transmission of data, added resource cost on the destination host to compute and reassemble the packet, etc.
Each layer the of TCP/IP model has its own packet size restriction. Even tho TCP has a maximum transit unit(MTU) of 65K bytes, in reality you will see much smaller packets being fragmented and distributed across multiple networks before arriving at the destination host. Every packet is assigned a unique sequence number and a byte count. This information is vital for ordered reassembly and consists of matching identification fields of incoming segments with those already held. A check sum is applied to every segment and computed at the sender, then recomputed at the destination host. An acknowledgment is sent back letting the sender know we have received the segment correctly. Typically each connection goes through setup, then data transfer, then closes connection.
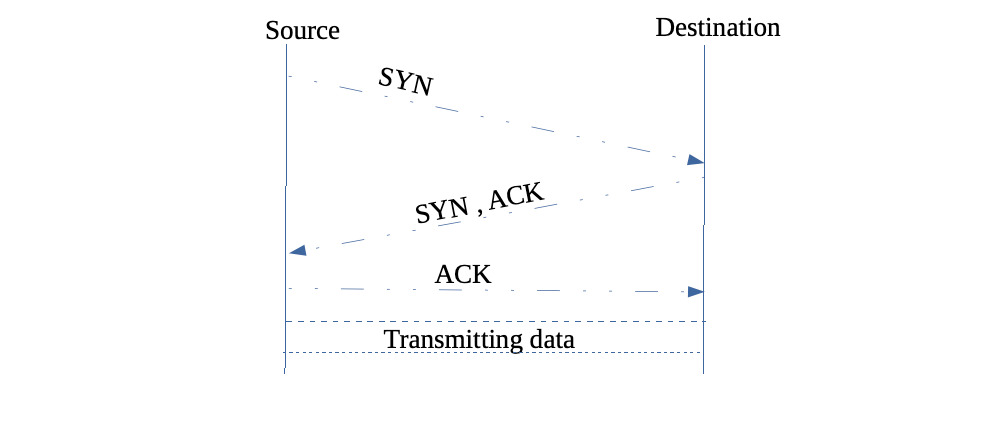
To establish a connection, the source host sends the destination host a SYN(synchronized) segment , which is just a packet with the syn bit flipped in the tcp flag field header. The destination host will send a response with its own SYN segment and acknowledges the connection with an ACK bit flipped. The source host must also acknowledge this connection with its own ACK segment. At this point communication setup is established over TCP and we can begin transferring data.
Now that we have a conceptual understanding of how information travels over TCP on a network. Let’s take a look at how all of this comes into practice.
For TCP analysis we will use tcpdump.
sudo apt install tcpdump
Let’s capture some packets and write it to a .pcap file so we can analyze our traffic with Wireshark.
sudo tcpdump -vv -w linuxjournal.pcap
-v for verbose (how detailed you want the output) -w tag writes to the .pcap file.
Now that we have some packets, let’s break out Wireshark for analysis.
sudo apt install wireshark
Open the .pcap file with Wireshark.
sudo wireshark linuxjournal.pcap
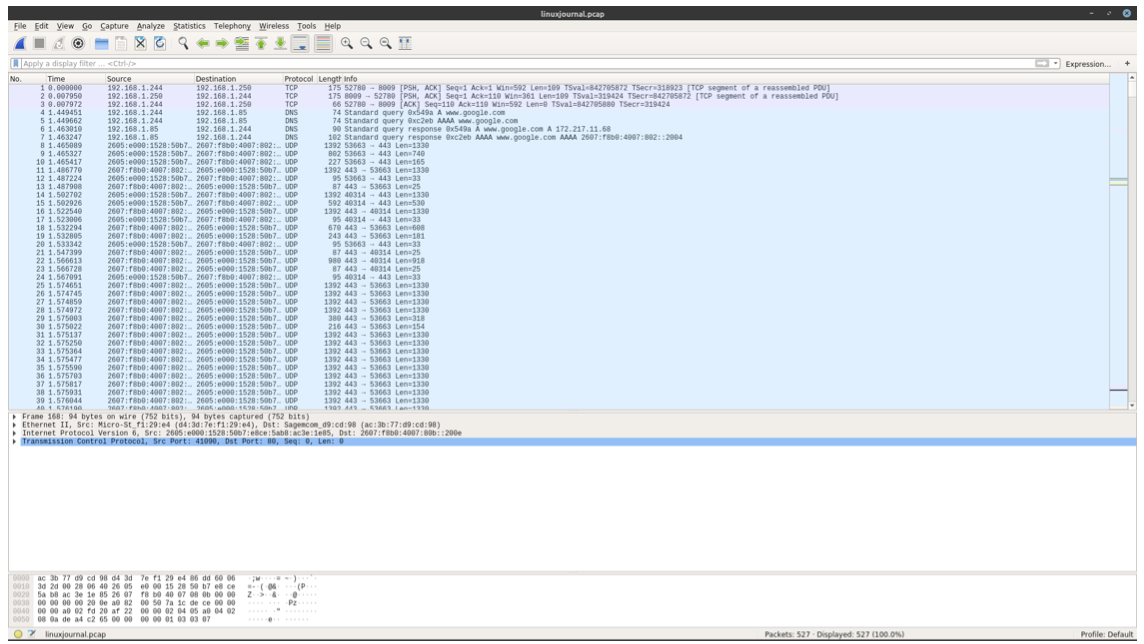
Filter the traffic for TCP only.
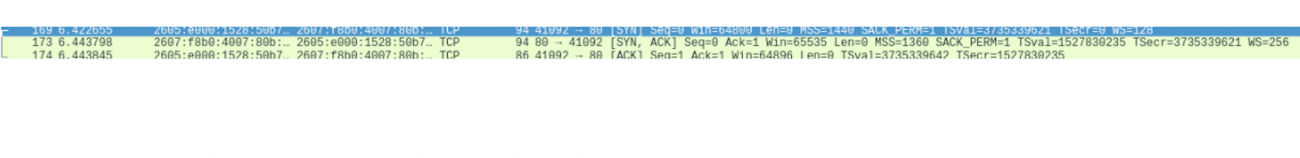
We can see some connections being established over tcp with a syn, syn ack, ack flag
Below we have some more detailed information about each specific packet. Click on the transmission control protocol drop down arrow below and take a look.
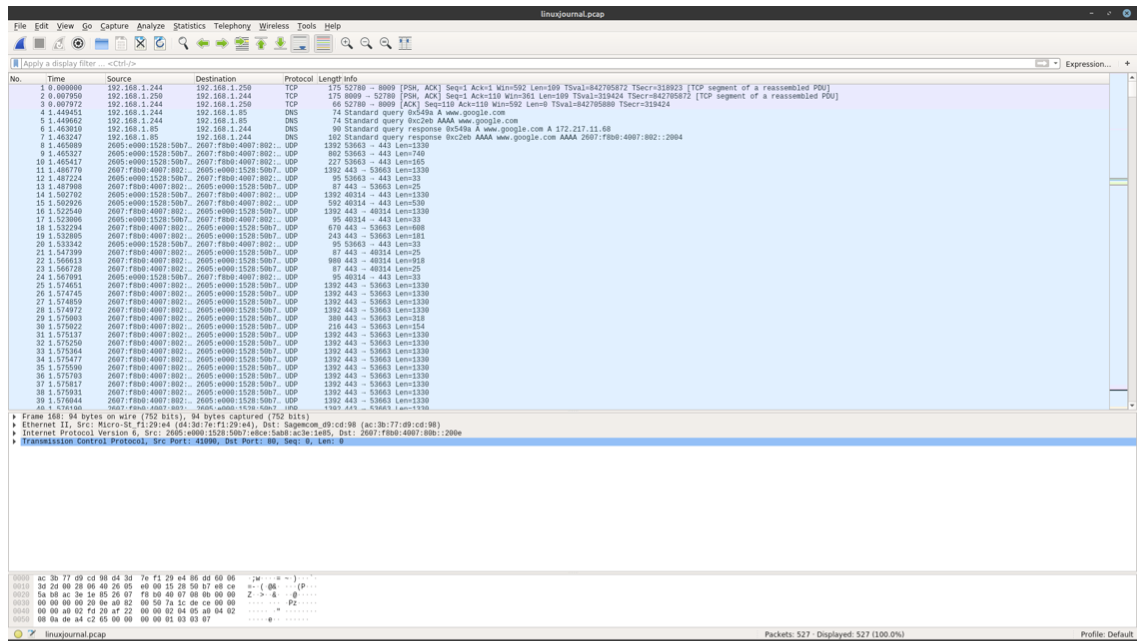
We see the source port and destination port. We have the segment length of 0 so we know data has not been sent. SYN flag field is flipped so the host is attempting to establish a connection.
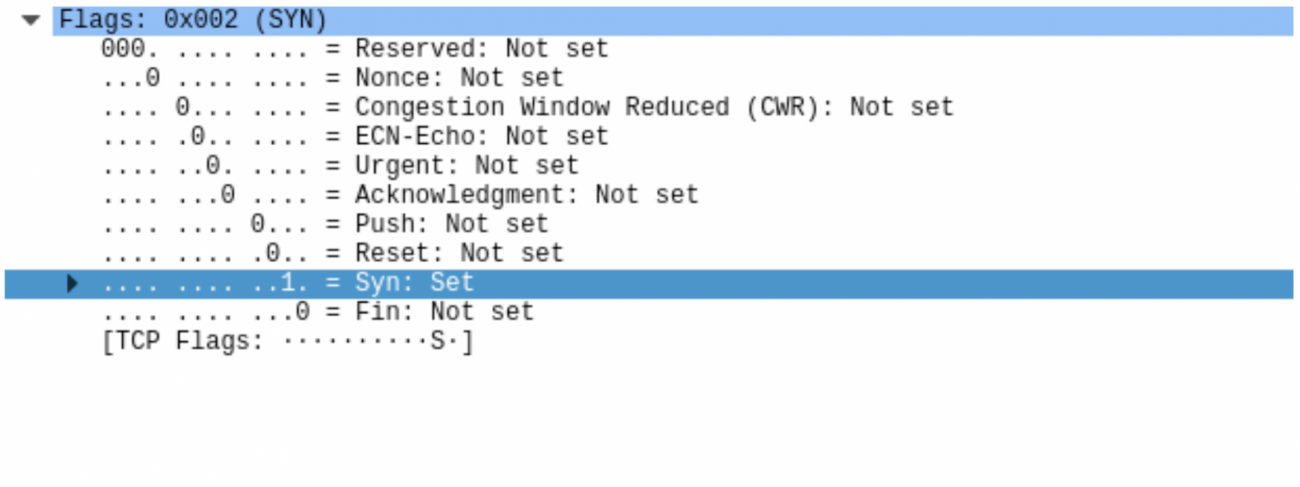
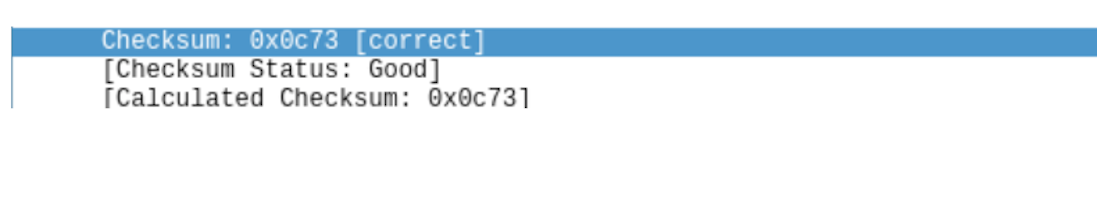
The checksum has been calculated correctly.
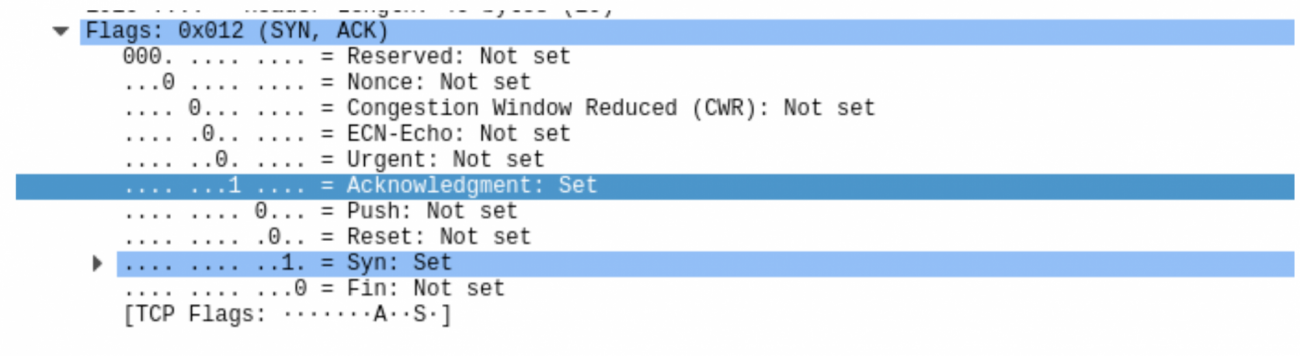
Stepping through to the next line we see have a syn ack sent back from our source to the destination host. The ack bit and syn bit are both flipped this time.
Our last line in setting up a connection has only the ack bit flipped
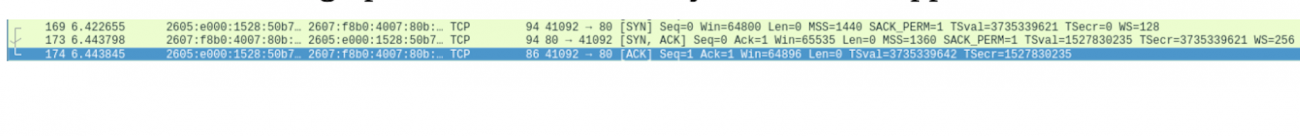
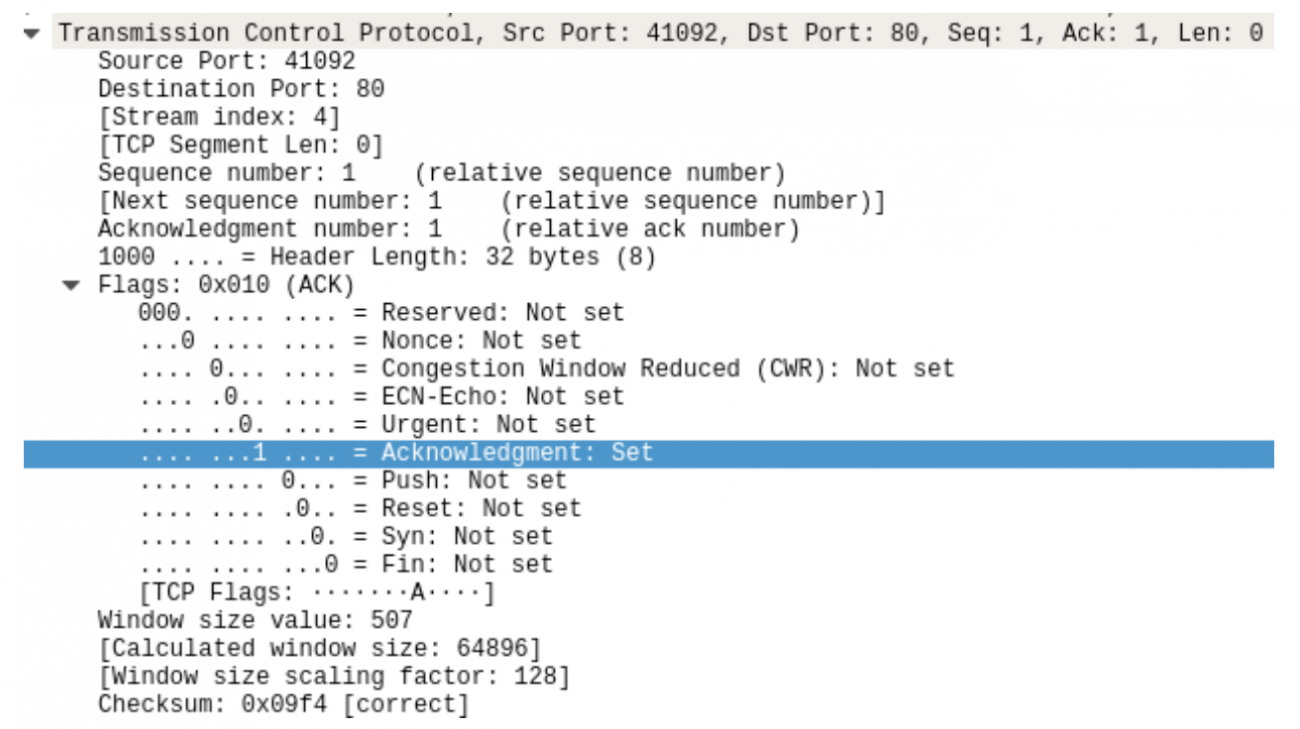
The connection between two hosts has been correctly established and we can begin transferring data.