|
You can now lock individual Amazon Elastic Block Store (Amazon EBS) snapshots in order to enforce better compliance with your data retention policies. Locked snapshots cannot be deleted until the lock is expired or released, giving you the power to keep critical backups safe from accidental or malicious deletion, including ransomware attacks.
The Need for Locking
AWS customers use EBS snapshots for backups, disaster recovery, data migration, and compliance. Customers in financial services and health care often need to meet specific compliance requirements, with prescribed time frames for retention, and also need to ensure that the snapshots are truly Write Once Read Many (WORM). In order to meet these requirements, customers have implemented solutions that use multiple AWS accounts with one-way “air gaps” between them.
EBS Snapshot Lock
The new EBS Snapshot Lock feature helps you to meet your retention and compliance requirements without the need for custom solutions. You can lock new and existing EBS snapshots using a lock duration that can range from one day to about 100 years. The snapshot is locked for the specified duration and cannot be deleted.
There are two lock modes:
Governance – This mode protects snapshots from deletions by all users. However, with the proper IAM permissions, the lock duration can be extended or shortened, the lock can be deleted, and the mode can be changed from Governance mode to Compliance mode.
Compliance – This mode protects snapshots from actions by the root user and all IAM users. After a cooling-off period of up to 72 hours, neither the snapshot nor the lock can be deleted until the lock duration expires, and the mode cannot be changed. With the proper IAM permissions the lock duration can be extended, but it cannot be shortened.
Snapshots in either mode can still be shared or copied. They can be archived to the low-cost Amazon EBS Snapshots Archive tier, and locks can be applied to snapshots that have already been archived.
Using Snapshot Lock
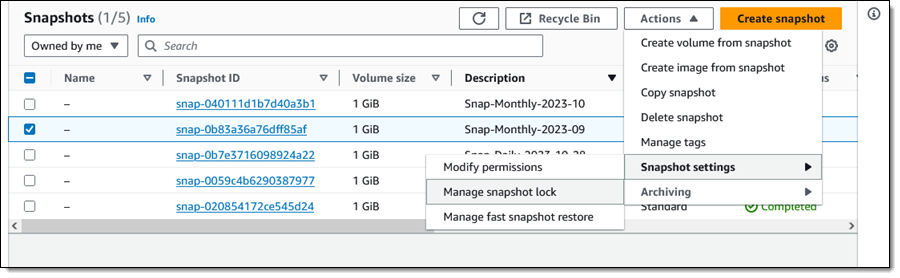
From the EBS Console I select a snapshot (Snap-Monthly-2023-09) and choose Manage snapshot lock from Snapshot Settings in the Actions menu:
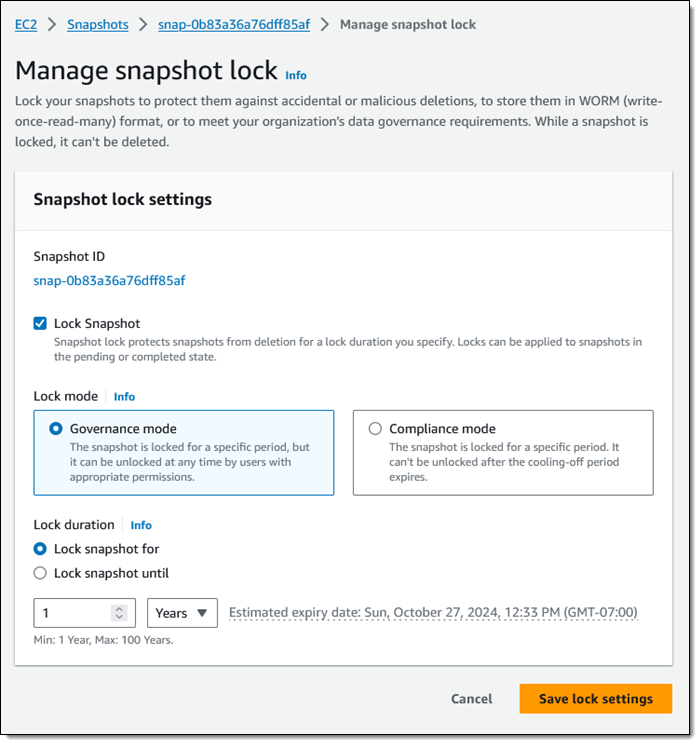
This is a monthly snapshot and I want to lock it for one year. I choose Governance mode and select the duration, then click Save lock settings:
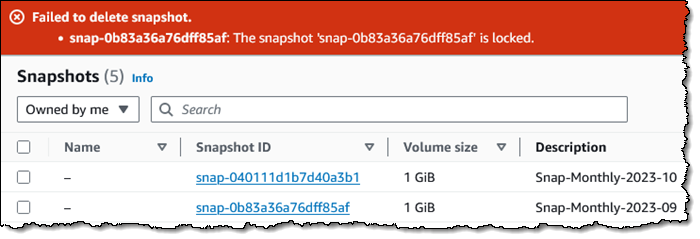
I try to delete it, and the deletion fails, as it should:
Now I would like to lock one of my annual snapshots for 5 years, using Compliance mode this time:
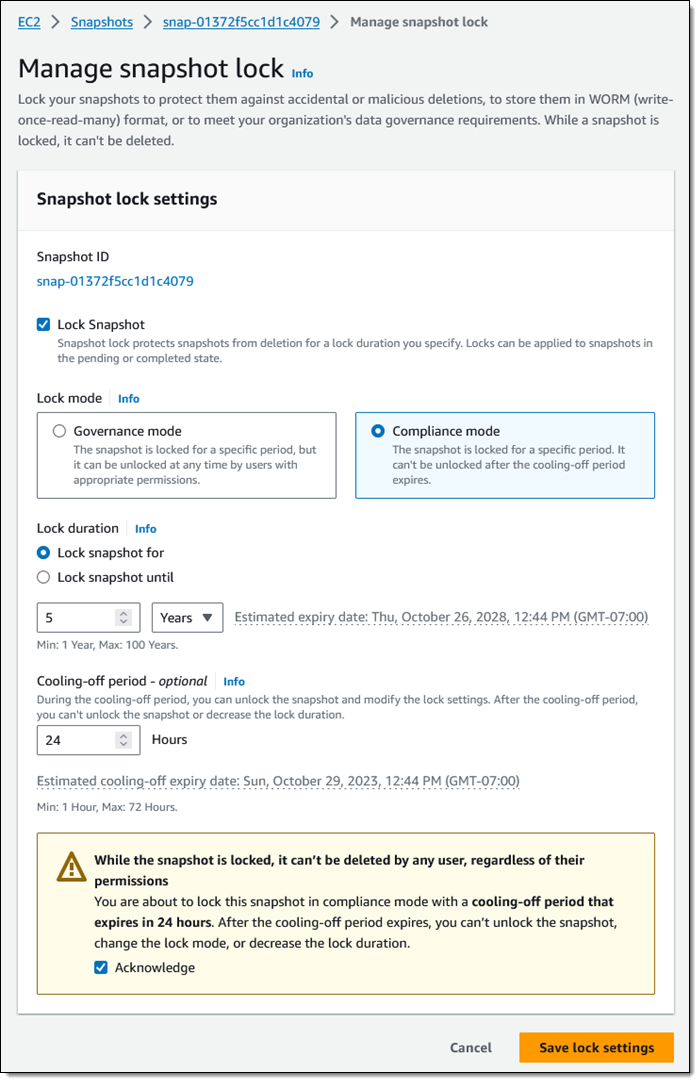
I set my cooling-off period to 24 hours, just in case I change my mind. Perhaps I have to run some kind of audit or final date validation on the snapshot before committing to keeping it around for five years.
Programmatically, I can use new API functions to establish and control locks on my EBS snapshots:
LockSnapshot – Lock a snapshot in governance or compliance mode, or modify the settings of a snapshot that is already locked.
UnlockSnapshot – Unlock a snapshot that is is governance mode, or is in compliance mode but within the cooling-off period.
DescribeLockedSnapshots – Get information about the lock status of my snapshots, with optional filtering based on the state of the lock.
IAM users must have the appropriate permissions (ec2:lockSnapshot, ec2:UnlockSnapshot, and ec2:DescribeLockedSnapshots) in order to use these functions.
Things to Know
Here are a couple of things to keep in mind about this new feature:
AWS Backup – AWS Backup independently manages retention for the snapshots that it creates. We do not recommend locking them.
Pricing – There is no extra charge for the use of this feature. You pay the usual rates for storage of snapshots and archived snapshots.
Regions – EBS Snapshot Locking is available in all commercial AWS Regions.
KMS Key Retention – If you are using customer-managed AWS Key Management Service (AWS KMS) keys to encrypt your EBS volumes and snapshots, you need to make sure that the key will remain valid for the lifetime of the snapshot.
— Jeff;